The MITRE ATT&CK Threat Analyzer is an experimental initiative developed with the Chief Data Scientist at Exabeam who pioneered the next-gen threat engine. This innovative technology leverages the power of the MITRE ATT&CK framework to significantly enhance cyber threat detection and analysis.
Based on the technical foundation, I created the interactive design prototype. The project was awarded a silver prize in a company hackathon and subsequently received a design patent for its unique interaction pattern. In this portfolio, I've further refined the original design by polishing the visuals and enhancing interactions, aiming to provide more polished vision for the advanced threat investigation tool.
Untangling the Web of Attacks:
Uncovering the attack chain is critical for successful cybersecurity investigations. However, traditional tools present limitations. They often offer network charts focusing solely on objects, such as actors, machines, and processes, or overwhelming lists of individual events and alerts with simple pattern analysis features. Analysts are left to weave these disparate pieces into a cohesive narrative, a time-consuming and challenging task.
The MITRE ATT&CK framework provides a valuable framework for understanding attack patterns and progression. Unfortunately, most SIEM vendors utilize it only for detection coverage. This underestimates the framework's potential, hindering the ability to comprehend evolving attacks.
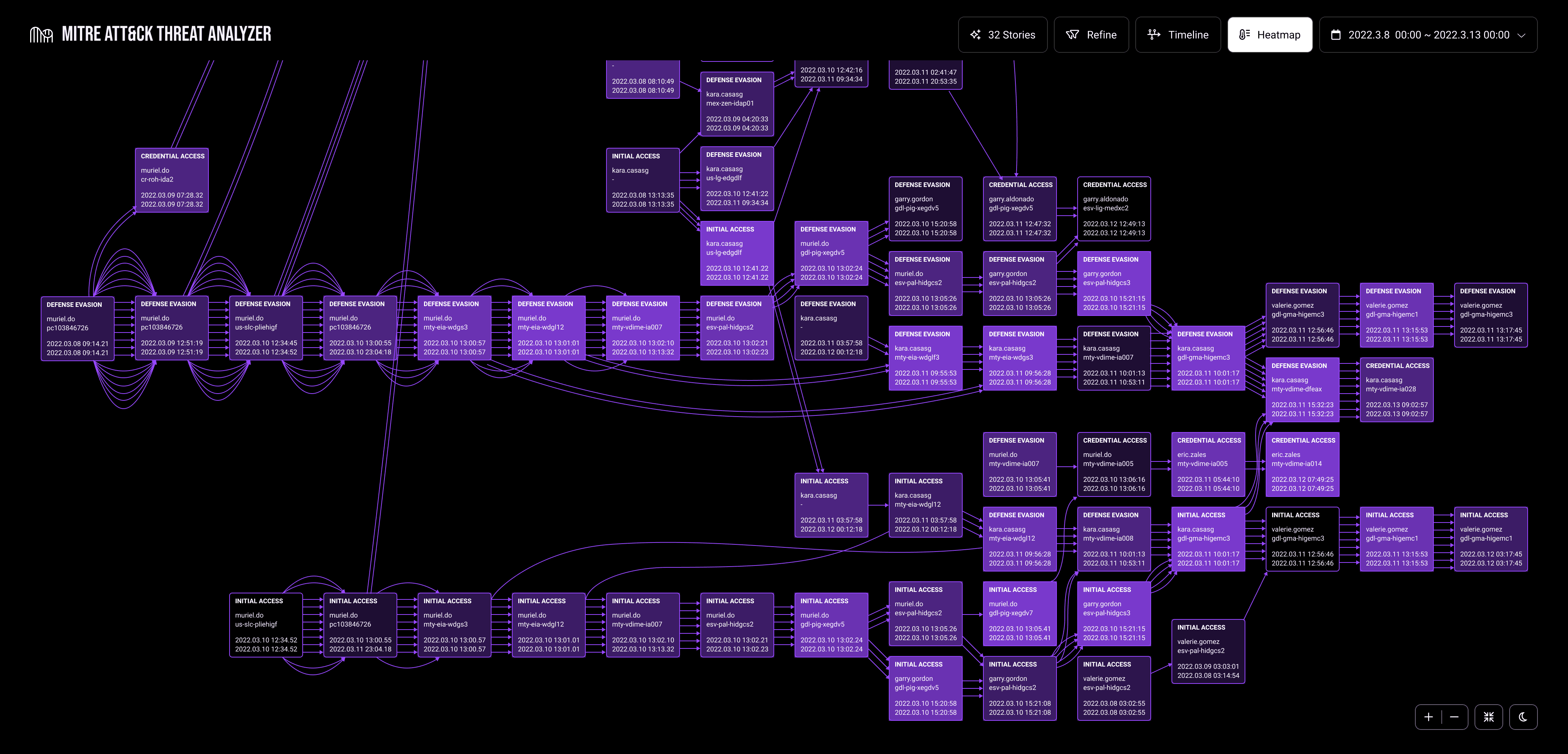
By leveraging the broader context provided by MITRE ATT&CK, investigators can identify attack chains. These are broader patterns that signal malicious behavior across various attack scenarios. This approach strengthens detection capabilities beyond isolated events, allowing analysts to proactively identify and mitigate ongoing or future threats.
Key Features of the MITRE ATT&CK Threat Analyzer:
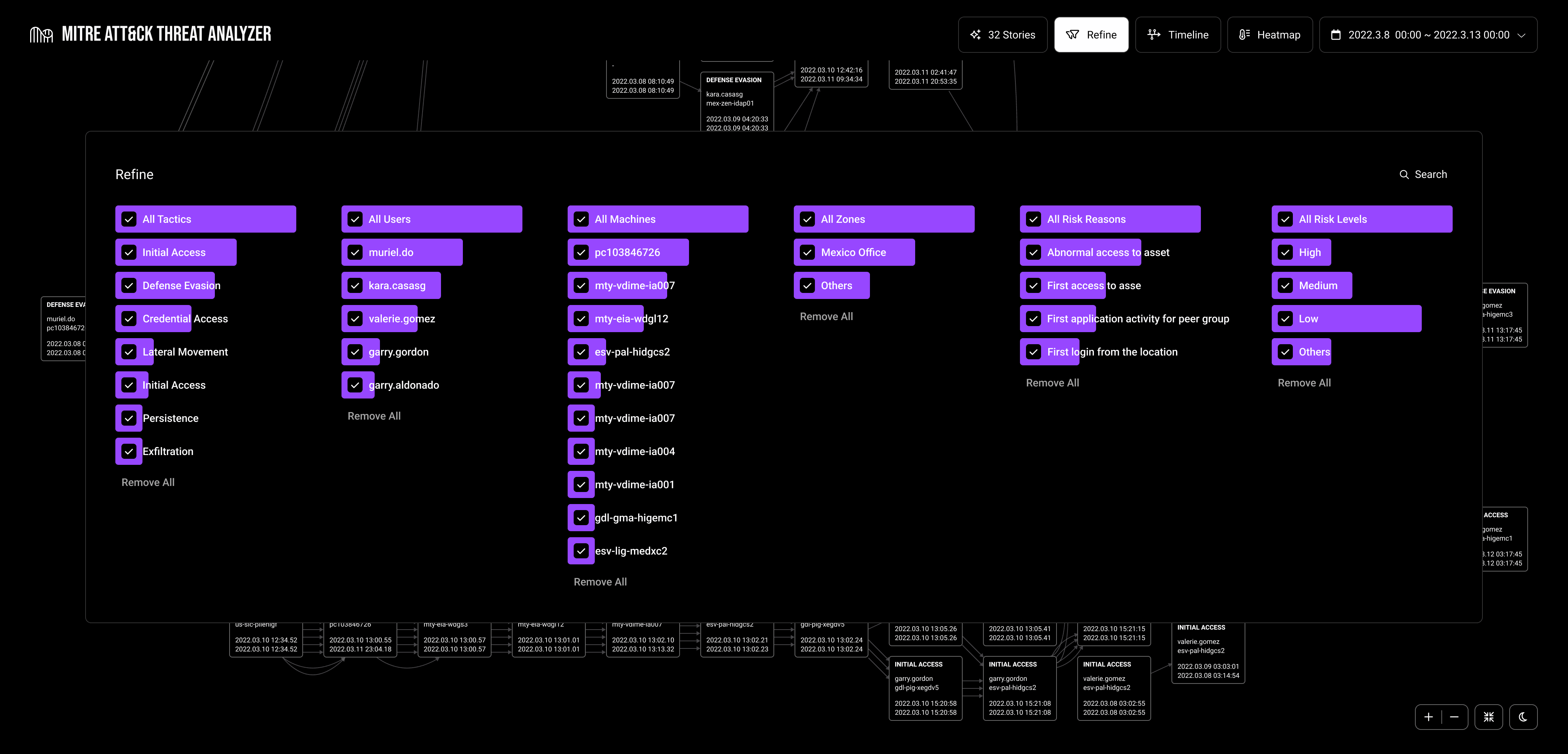
Advanced Interactive Visualizations: We utilize innovative visualizations that map potential attack pathways based on the MITRE ATT&CK tactics.
Graph-Based Approach: This visualization approach provides a clear picture of the relationships between attack steps. It correlates Indicators of Compromise (IOCs), allowing analysts to quickly grasp the attack narratives.
Coherent Threat Assessment: Equipped with this clear visual representation, analysts can rapidly assess the scope, stage, and severity of potential cyber threats.