exabeam
investigation workbench
seamless security- Where Smart Workflows Meet Modern Investigation
CASE STUDY / APR. 2020
Download Case Study
The Investigation Workbench, originally launched as an auxiliary service to our on-premises advanced analytics platform nearly eight years ago, marked the beginning of our journey in enhancing cybersecurity investigation tools.
In 2018, we set forth on an ambitious path with a renewed vision: to position ourselves as a frontrunner in the cloud-based cybersecurity arena. This strategic pivot involved a shift towards developing cloud-native applications, signaling a departure from our legacy on-premises solutions.
The cybersecurity environment is one that evolves at breakneck speed, spurred by technological breakthroughs and the advent of new market players. In response to this dynamic landscape, our clients voiced a critical demand for an upgraded workbench that could harness the power of machine learning and automation to bolster their investigative capabilities.
It was during this period of transformation that I had the opportunity to contribute to a highly strategic initiative: the comprehensive overhaul of the Investigation Workbench for our rapidly expanding startup in the cybersecurity sector. This project was not just about updating technology; it was about reimagining how cybersecurity investigations could be conducted in the cloud era, ensuring our solutions were at the forefront of innovation and utility.
Reimagining Cybersecurity: A Vision for the Future
The primary objective of this project was to revolutionize the entire user experience, with a particular emphasis on optimizing the investigation workflow. Our aim was to redefine the company's identity, positioning ourselves as the leading solution in User and Entity Behavior Analytics (UEBA) on the market.
Moreover, an essential part of our strategy involved modernizing the product's aesthetics to align with our recently established style guide, which has already been applied to our latest cloud-native offerings.
Our ambitions were driven by the need to establish a robust platform capable of withstanding intense market competition and meeting the increasingly sophisticated requirements of our users.
To achieve this, our high-level goals included:
Crafting a Comprehensive Vision: Developing a holistic end-to-end (E2E) vision for the Investigation Workbench that not only meets current expectations but also anticipates future needs.
Bridging the Gap: Ensuring a fluid and seamless workflow that integrates the traditional strengths of our platform with the innovative features of our new cloud-native solutions.
Revitalizing the User Interface: Refreshing the product's appearance by implementing the new style guide, thereby enhancing the overall look and feel to reflect our forward-thinking ethos.
Through these objectives, we aimed to not just update a product but to transform the way cybersecurity investigations are conducted, making our tool an indispensable asset in the cybersecurity toolkit.
discovery
design workshop
3 days
We organized a comprehensive three-day design workshop dedicated to deep diving into the customer journey. This involved a detailed examination of existing workflows, pinpointing challenges, and identifying opportunities for improvement. Utilizing empathy maps and "Who+Do" exercises, we engaged with customer advocates and security experts to gain a nuanced understanding of the user experience.
Personas
Customer Empathy Map
Journey Map
INTERVIEWS
10 customers
We engaged in meaningful conversations with 10 of our customers, aiming to cultivate a deeper comprehension and gather insights. This process was instrumental in validating our hypotheses and uncovering valuable opportunities for innovative solutions.
Needsfinding
Concept Validation
Co-designing
HEURISTIC EVALUATION
12 hrs
We invested effort in thoroughly evaluating the current system's workflows and interfaces to uncover core challenges. This process enabled us to identify critical usability issues and system patterns, leading to the creation of a focused list of areas for improvement. These insights were instrumental in shaping the information architecture and establishing guiding principles for the design of future solutions.
Usability
System, Patterns
Information Architecture

soc personas
Security Operation Center (SOC) teams operate within a highly organized workflow, characterized by clearly delineated roles and responsibilities. Our research identified a common structure consisting of five key roles: three levels of security analysts, security engineers, and a managerial position. Additionally, certain organizations feature a specialized insider threat team tasked with scrutinizing potentially malicious activities by employees. While each role focuses on distinct aspects of security, effective communication and collaboration are paramount for the collective success of the team.

Tier 1 Analyst
Tim
Tier 1 Analysts are the frontline defenders, monitoring systems and alerts to detect potential security incidents. They perform initial assessments and escalate confirmed threats to Tier 2.
Tier 2 Analyst
Ivy
Tier 2 Analysts delve deeper into the escalated alerts, conducting thorough investigations to understand the scope and impact. They may also initiate containment measures.
Tier 3 Analyst
Hunter
Tier 3 Analysts are the most experienced and handle the most complex investigations. They develop threat hunting strategies to identify hidden threats and work on complex incident response and remediation.
security engineer
esteban
Security Engineers design and implement the organization's security infrastructure. They develop security measures to protect systems against attacks, conduct regular security assessments, and are involved in the development and fine-tuning of automated security solutions.
SOC Manager
Corri
The SOC Manager oversees the entire SOC team, ensuring that security procedures are followed, and goals are met. They coordinate incident response efforts, manage the team's budget and resources,
insider threat team
india
This specialized team focuses on identifying and mitigating risks posed by insiders. They monitor user behaviors, conduct risk assessments, and investigate suspicious activities to protect against internal threats.
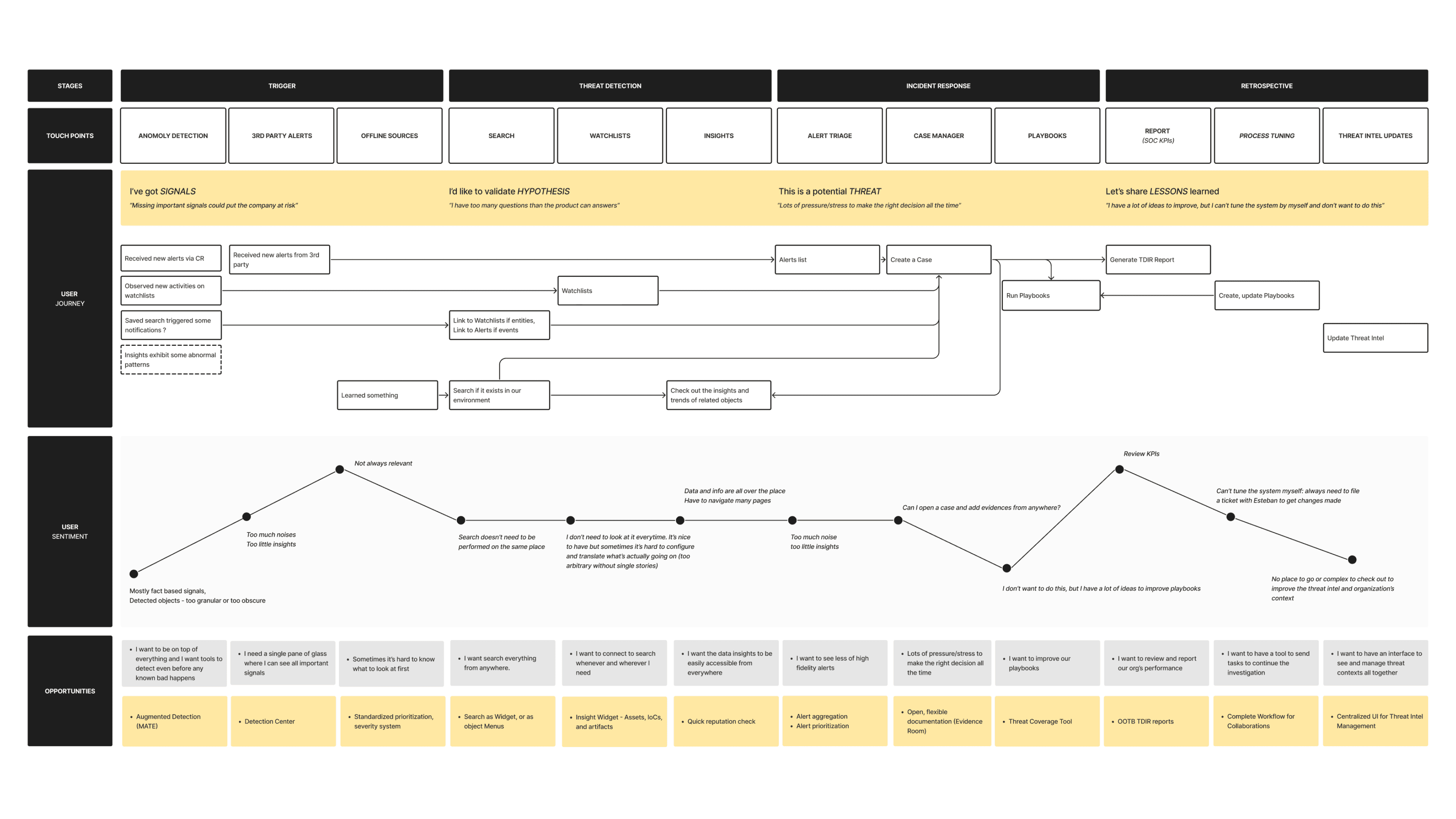
customer JOURNEY MAP
The creation of a journey map proved to be an invaluable exercise for our team, offering a comprehensive view of the analysts' workflow, including all the touchpoints both within and outside the product's areas. This holistic perspective enabled the team to generate a lot of interesting concepts without losing sight of the full picture, allowing us to identify key areas of focus.
More importantly, this exercise shed light on the current state of our customer interactions, revealing the complete narratives of their experiences, the challenges they face, and their unmet needs. By meticulously mapping out each step of the analysts' journey, we were able to pinpoint specific moments where our product could either enhance the user experience or fall short of expectations.
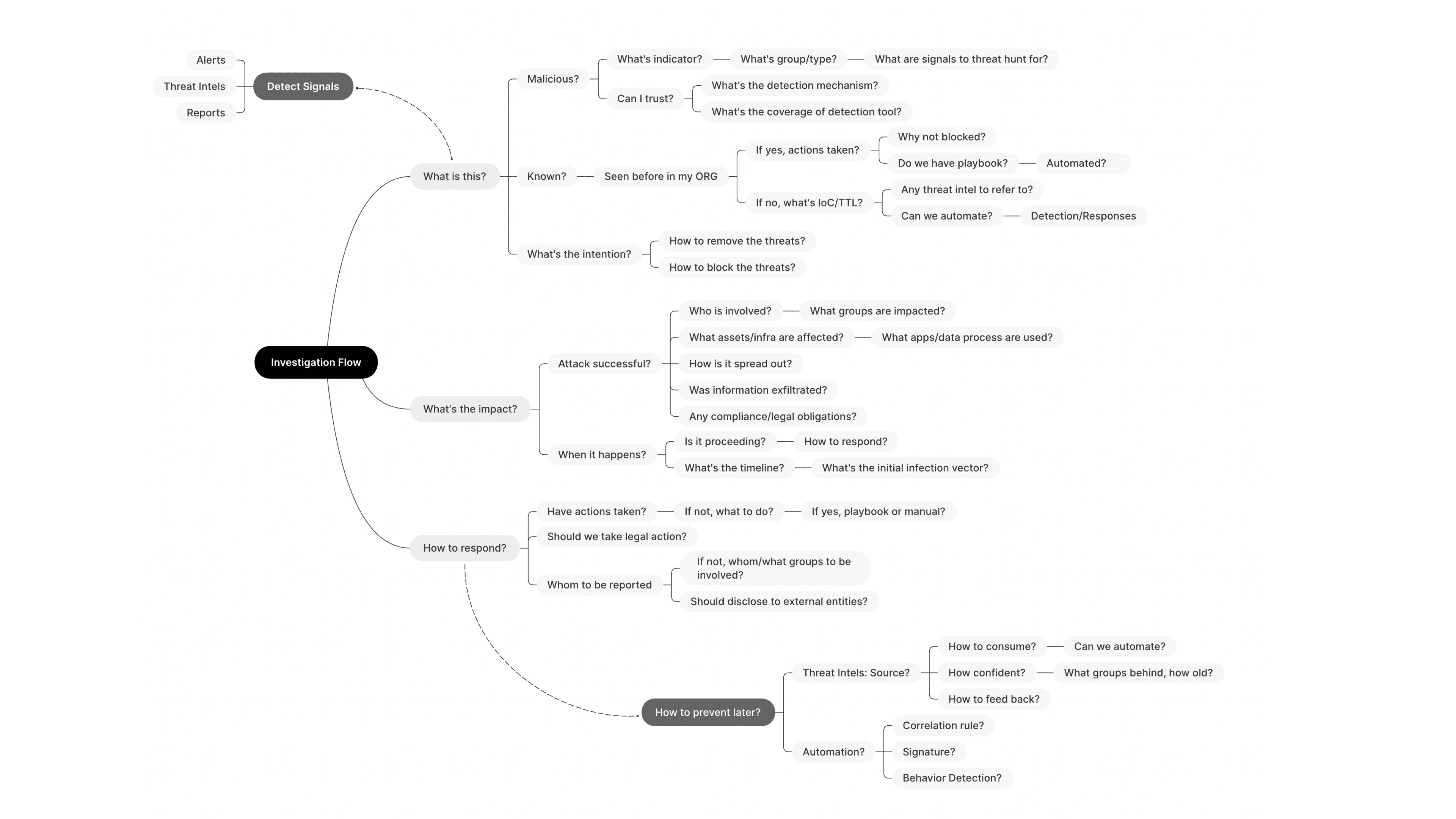
ANALYST mental model
In tandem with the journey map, which delineates the end-to-end steps of users through their workflows, I've developed an analyst's mental model. This model serves to chart the internal thought processes and decision-making patterns of our users. This exercise has proven to be an invaluable artifact, offering profound insights that will inform our design strategy. It enables us to precisely identify the types of tools, features, and layouts that should be prioritized in our solution development, ensuring that we align closely with the user's cognitive flow and operational needs. This mental model has become a cornerstone in our approach, guiding us to create solutions that are not only functional but also intuitive, reflecting the natural thought processes of our customers.
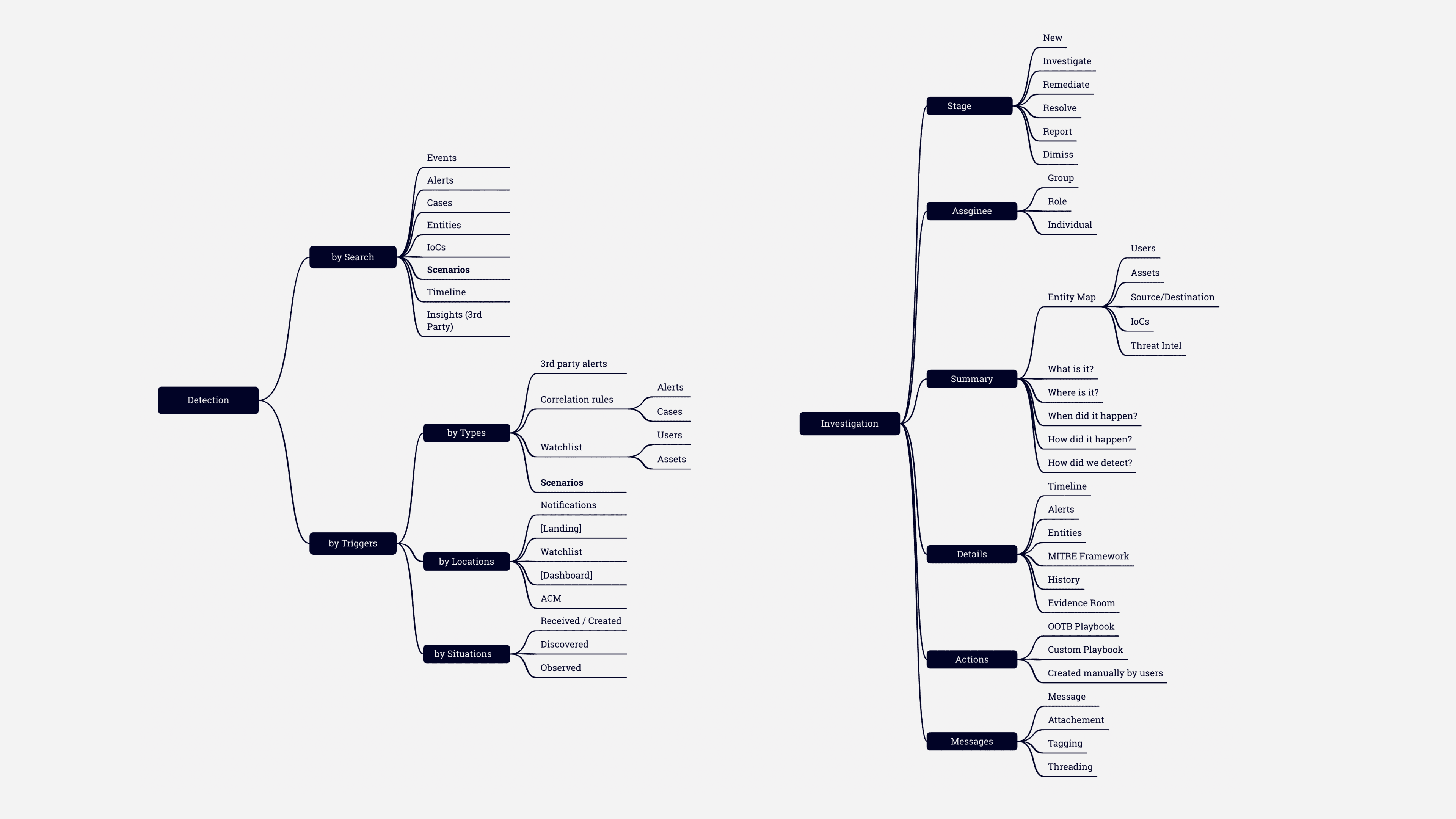
information architecture
In addressing the information architecture of our platform, I quickly mapped out the various objects, features, and space types that span from detections to investigations.
This process helped further:
Object Classification: Defining the key entities within our system, such as alerts, incidents, and cases, and understanding their attributes and relationships
Feature Organization: Categorizing the features according to their use cases, ensuring that users can navigate easily between different functionalities without losing context.
Spatial Layout Design: Determining how objects and features are presented in the user interface, including the spatial relationships between different elements.
layout exploration
In the layout exploration phase, we meticulously designed and tested four distinct layout options to determine the most efficient and effective interface for our users. The designs ranged from a simple list view to a more complex grid layout, each with its unique advantages and tailored to different user needs.
We conducted rapid testing with internal users utilizing mock data to evaluate the efficiency and effectiveness of each layout. The feedback gathered was crucial in identifying which design best supported the workflow, enhanced user productivity, and met the demands of complex security investigations. This iterative process is pivotal in our commitment to delivering a user-centric product that meets the high standards required by SOC teams.

highlights
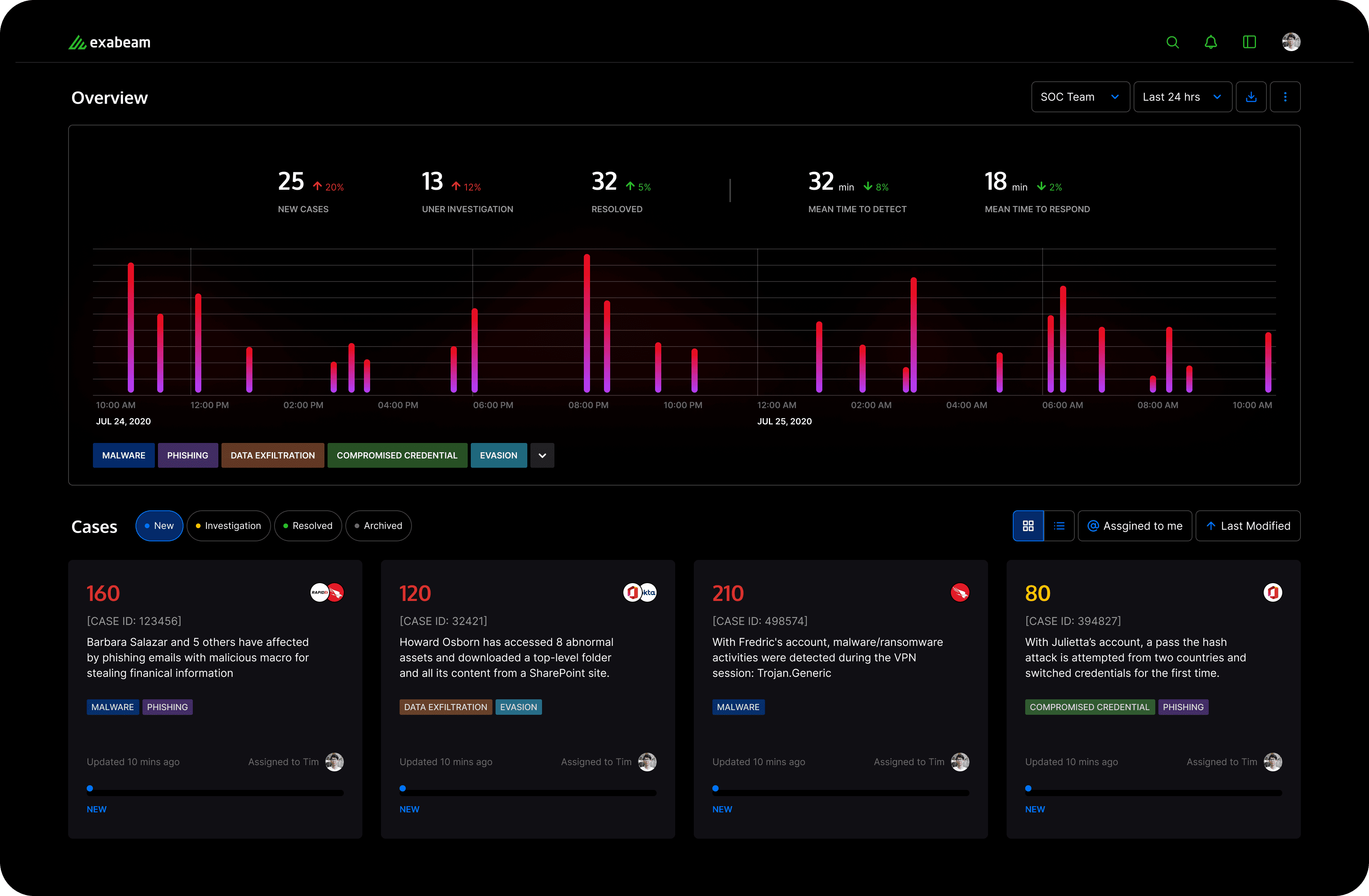
LESS ALERTS, MORE WORK DONE: SMART AGGREGATION
The landing interface of the case manager is deliberately designed to present prioritized data upfront. It greets users with a clear display of KPIs and a timeline chart that incorporates MITRE filters for an immediate overview of the threat landscape.
Our automated aggregation transforms numerous alerts into a digestible stream of significant events via our advanced contextual engine. To further enhance an analyst’s ability to prioritize efficiently, we've introduced an aggregated score for each event, serving as a singular, comprehensive indicator of priority.
These scored cases are then displayed along a timeline, embedding the vital dimension of time directly into the context, which is essential for understanding the evolution and urgency of threats.
Following this, the grid layout showcases only the most pertinent cases—those that are new and specifically assigned to the user, ensuring a highly personalized and distraction-free experience from the moment they log in.
VICTIMS OR ACTORS?:
inline actor context
Placing users and assets at the center of the investigation process is critical. With a comprehensive understanding of their backgrounds, activities, and occasionally even their narratives that may not appear directly relevant to the case, holds great importance.
Enabling analysts to access complete profiles and timelines with a single click, without having to leave the user interface, can significantly expedite the investigation process.
Exabeam holds a significant advantage over its competitors with its robust UEBA features. Our design effectively harnesses the power of UEBA and seamlessly integrates it into the user workflow, providing quick access to relevant information from anywhere within the system.
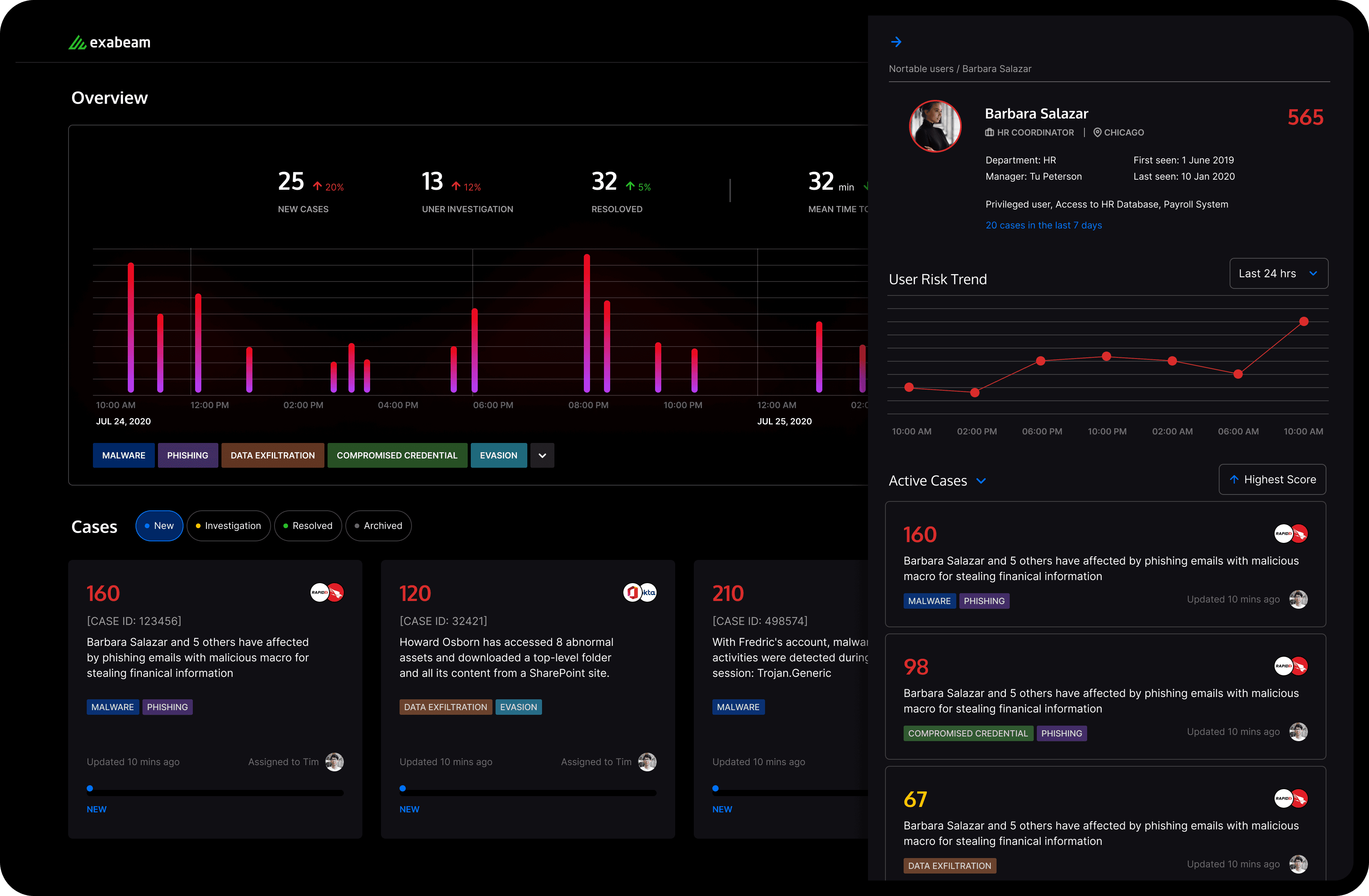
actionable case manager with smart summary
Upon opening a case within our case manager, users are presented with a smart summary that offers both visual and textual data in a condensed form. This summary is designed to give analysts an immediate understanding of the connections between actors, machines, and artifacts, as well as insights generated by our context engine. It provides a clear narrative based on the critical parameters of what, where, when, and how.
Furthermore, any related artifacts, actors, and assets are not just displayed in isolation; they are enhanced with intelligence from our threat intel database and given additional depth with organizational context, all of which become instantly accessible with a simple mouse hover.
To navigate the subsequent steps in the investigation or remediation process, the case manager guides users with a clear sequence of actions. It simplifies collaboration by allowing any of these actions to be assigned to team members directly within the platform. This functionality ensures that moving forward with a case is as streamlined and collaborative as possible, enabling teams to act efficiently and effectively.
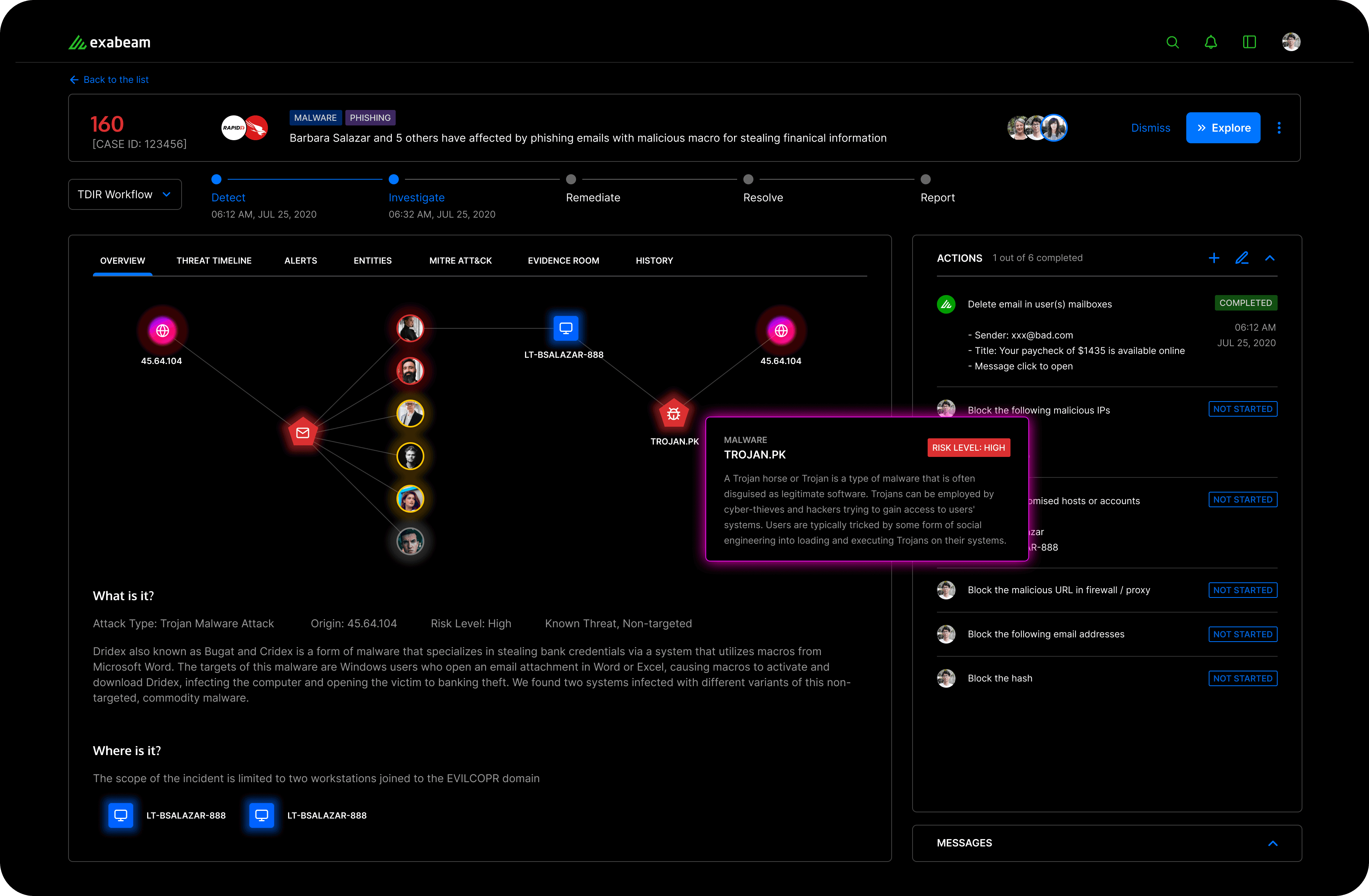
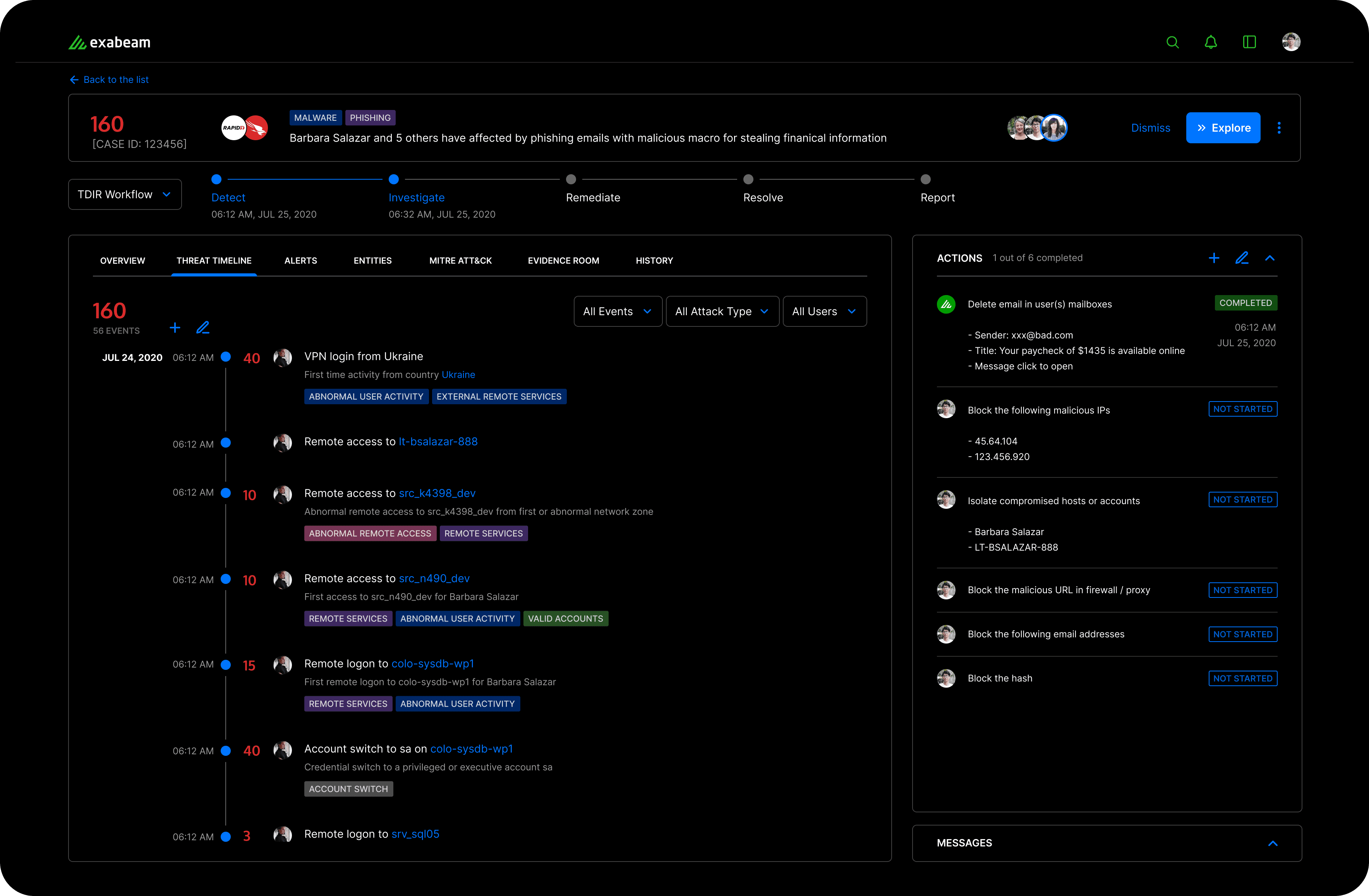
Clarity in Complexity: Uncover Attack Stories Effortlessly
Our design presents events of interest in a cohesive timeline view, laying out the narrative of an attack clearly and concisely. This user-friendly design provides a straightforward understanding of the attack's progression at a glance. For those seeking in-depth details, a progressive disclosure design element reveals extensive event data, including processed logs, with just a click. This enhanced timeline is a significant evolution from the original version, marrying simplicity with depth.
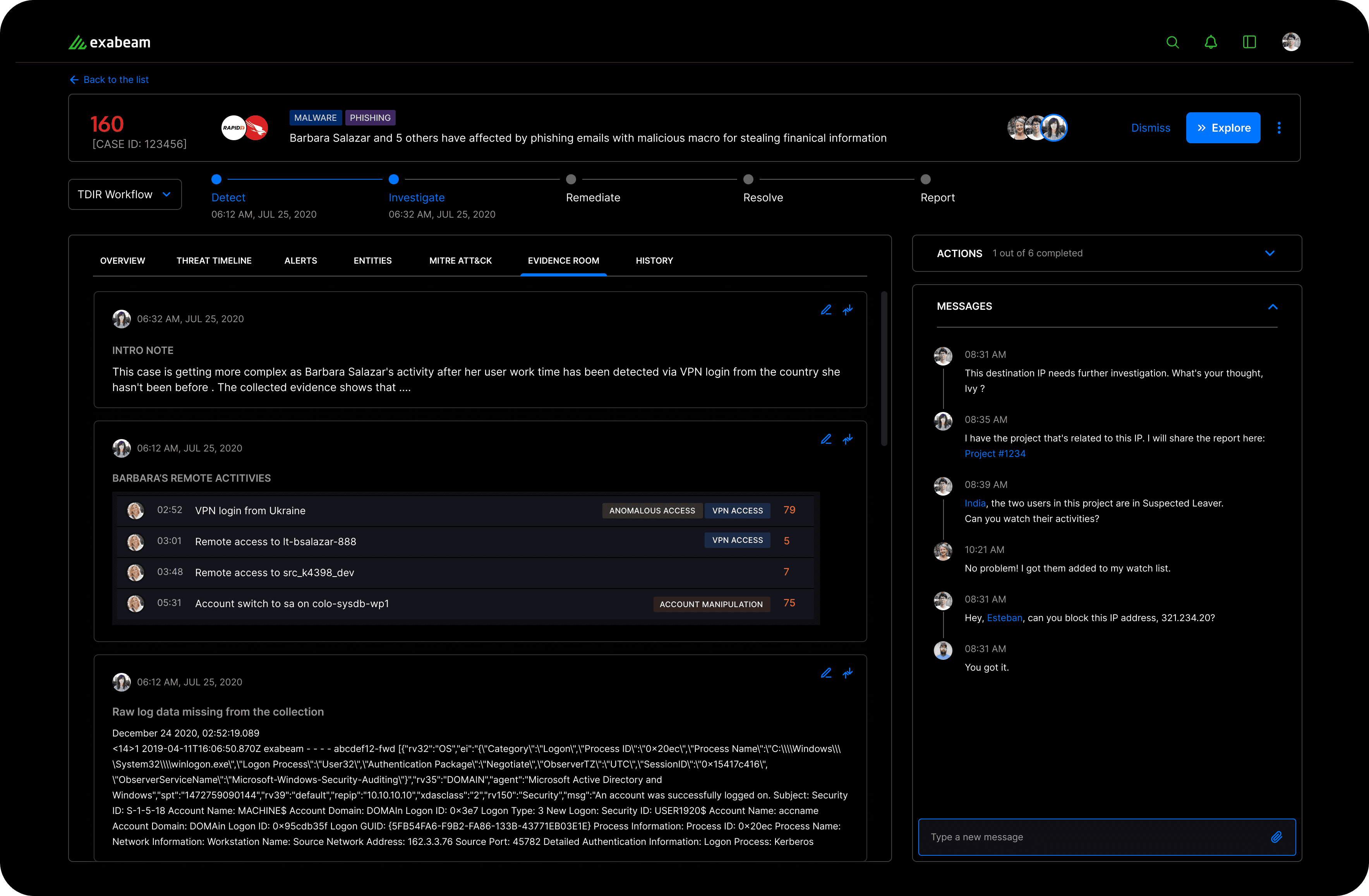
OPEN, FLEXIBLE WORKSPACE:
EVIDENCE ROOM
Closed investigation tools always expose their limitations, despite how many tools and enriched objects they provide. It's not merely a matter of insufficient offerings by advanced investigation apps; there are always unstructured data sets that remain overlooked. Analysts don't want too many constraints.
Openness is the pivotal element. By providing analysts with an open space, they can freely gather diverse types of data and artifacts that suit their needs. This flexibility empowers analysts to explore various avenues of investigation without being hindered by rigid boundaries.
Additionally, analysts often find value in sharing their analyses and descriptions as documentation and fostering collaborative sharing among their peers.
retro
Reflecting on our project's journey, it's clear that allowing design to lead the way, unshackled by traditional requirements, has been instrumental in reshaping the user experience and perception. The debut of our redesigned features didn't just introduce new functionalities; it boldly reenvisioned the user journey, enhancing engagement, efficiency, and overall satisfaction significantly. This approach of design-driven innovation was pivotal, setting a new benchmark for how we develop and refine our product.
Design-Driven Product Development: By prioritizing user goals over strict product requirements, we were able to explore innovative solutions that truly resonated with our users. This freedom allowed us to craft an experience that was not just functional but also intuitive and delightful, marking a departure from the traditional development process.
Engagement with Unhappy Customers: Proactively reaching out to dissatisfied customers turned out to be a golden opportunity. Not only did this engagement provide us with invaluable insights, but it also helped us forge stronger relationships. Through open dialogue and genuine concern for their experiences, we transformed challenges into testimonies of our commitment to user satisfaction.
Innovative Breakthroughs: Our journey underscored that innovation doesn't stem from merely replicating what exists but from daring to break the mold, even in small, impactful ways. Our streamlined workflow, seamlessly integrating search with visual analysis, exemplifies this principle. This breakthrough significantly improved the user experience, proving that thoughtful deviations from the norm can lead to substantial enhancements.
Moving forward, the insights gained from this project will continue to influence our strategy. The tangible benefits we've seen, from heightened user satisfaction to stronger retention rates, highlight the value of a design-first approach. Our dedication to incorporating user feedback and fostering a community around our product is unwavering. This project marks not an end but the beginning of a journey towards a more inclusive, innovative, and user-centered future.
Key Achievements
system usability score
+19.6
Following the phased roll-out of our new product features, we observed a notable improvement in our System Usability Scale (SUS) scores in comparison to those of our legacy case manager.
true positive
99%
Our testing confirmed a remarkable 99% accuracy rate for high and low priority alerts identified by our new alert aggregation engine. This marks a significant advancement from industry standards, where it's reported that traditional SIEMs experience a false positive rate of about 33%.
average clicks
< 0.2%
Users have reported a substantial reduction in time spent, with fewer interruptions from navigating between screens. This efficiency has enabled them to manage tasks entirely within the case manager, eliminating the need to switch to other pages.
