This is for show casing some exploratory design for visualizations I've been researching on around key use cases for SIEM. SIEM has proactively adopted visualizations in order to provide summary of massive data, surface patterns and abnormalities, and some vendors introduced advanced visualization tools where analysts can get their answers.
I have been always fascinated by the functional beauty and fascinating insights creative visualizations can bring to the product experience. Some of my projects involved some visualization features, but the depth of them were not very deeply requests, so I determined to spend some of my time to explore this exciting visualizations as my personal projects and here are some of the results I've made.
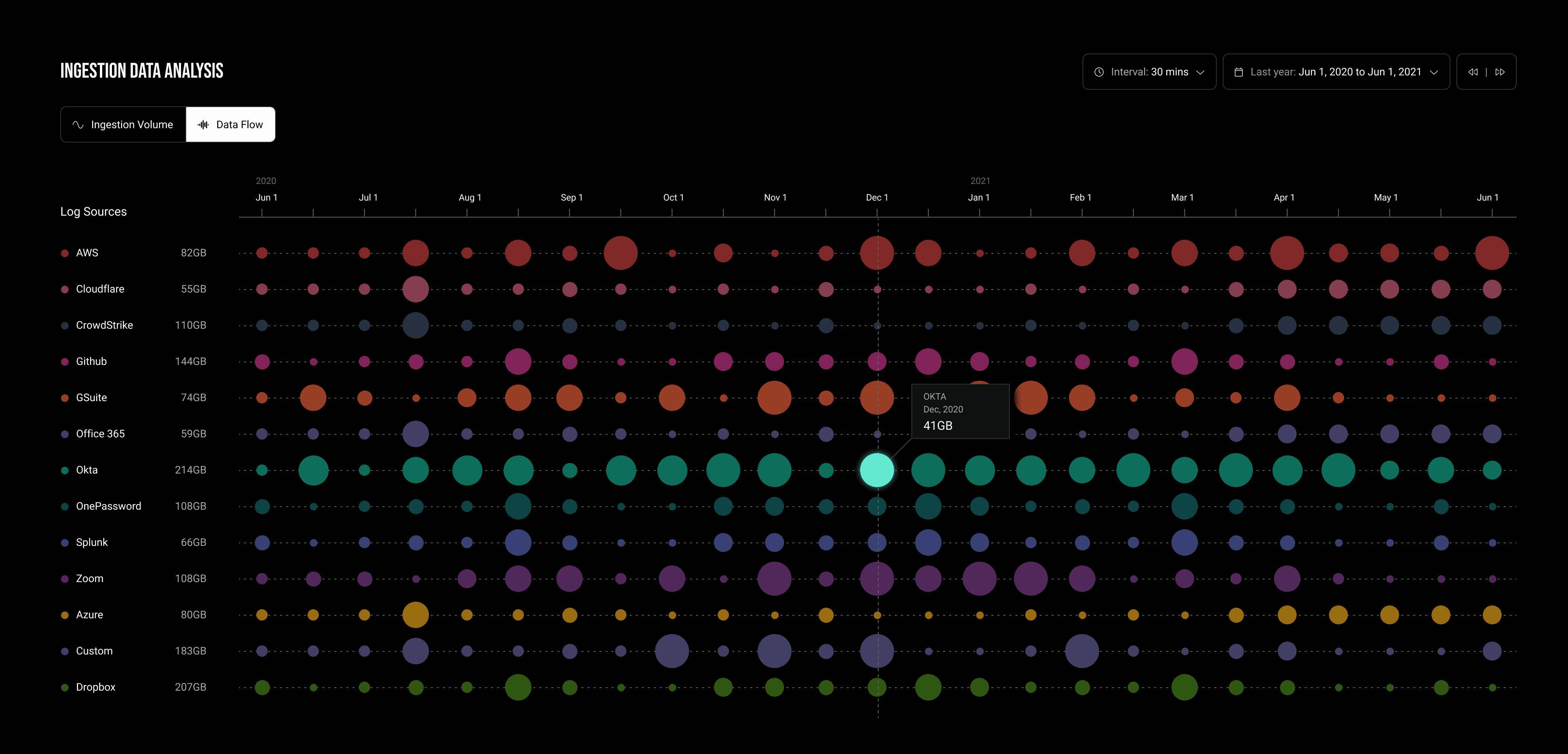
Data ingestion monitoring in cybersecurity systems is a critical process that involves tracking, managing, and analyzing the flow of data from various sources. This process is essential for ensuring the system can effectively perform its core functions. In my design exercises, I've investigated two kinds of data visualizations
Ingestion Volumes Over Time by Data Sources:
This visualization tracks the volume of data ingested over time from various sources, identifying trends, peak data influx periods, and potential data collection inconsistencies.
Ingestion Flows by Data Sources:
By employing a Sankey chart, I was able to map out the flow of ingested data through the system, from the initial data intake to normalization and detection creation, effectively showcasing the data's journey and transformation.
The MITRE ATT&CK framework is a critical tool for organizations looking to strengthen their security posture. It goes beyond simply listing threats – it provides a comprehensive understanding of attack patterns and techniques, allowing organizations to identify gaps in their detection coverage and manage their security measures more effectively.
This vision leverages the power of the ATT&CK framework by creating a coverage map with progressive interactions. Users can start with a simple visual indicator and then deep dive into the full context of individual techniques. This leads to a comprehensive analysis of detection capabilities, along with smart suggestions to improve coverage and better protect their organization.
In the cybersecurity investigations, uncovering the attack chain is crucial for understanding how attackers compromised a system. Combining the MITRE ATT&CK framework with event timeline analysis unlocks one of the most powerful tools in investigation.
By consolidating event data with the MITRE framwork, investigators can map individual events to specific TTPs within the attack chain. This unveils a chronological narrative of the attack, revealing the sequence and methodology used by the attackers.
This approach goes beyond simple Indicators of Compromise (IOCs), which are static and often specific to individual attacks. Instead, by leveraging the broader context provided by MITRE ATT&CK, investigators can identify Indicators of Activity (IOAs) – broader patterns that signal malicious behavior across different attack scenarios. This enhances detection capabilities beyond individual events, allowing analysts to identify and mitigate ongoing or future threats.